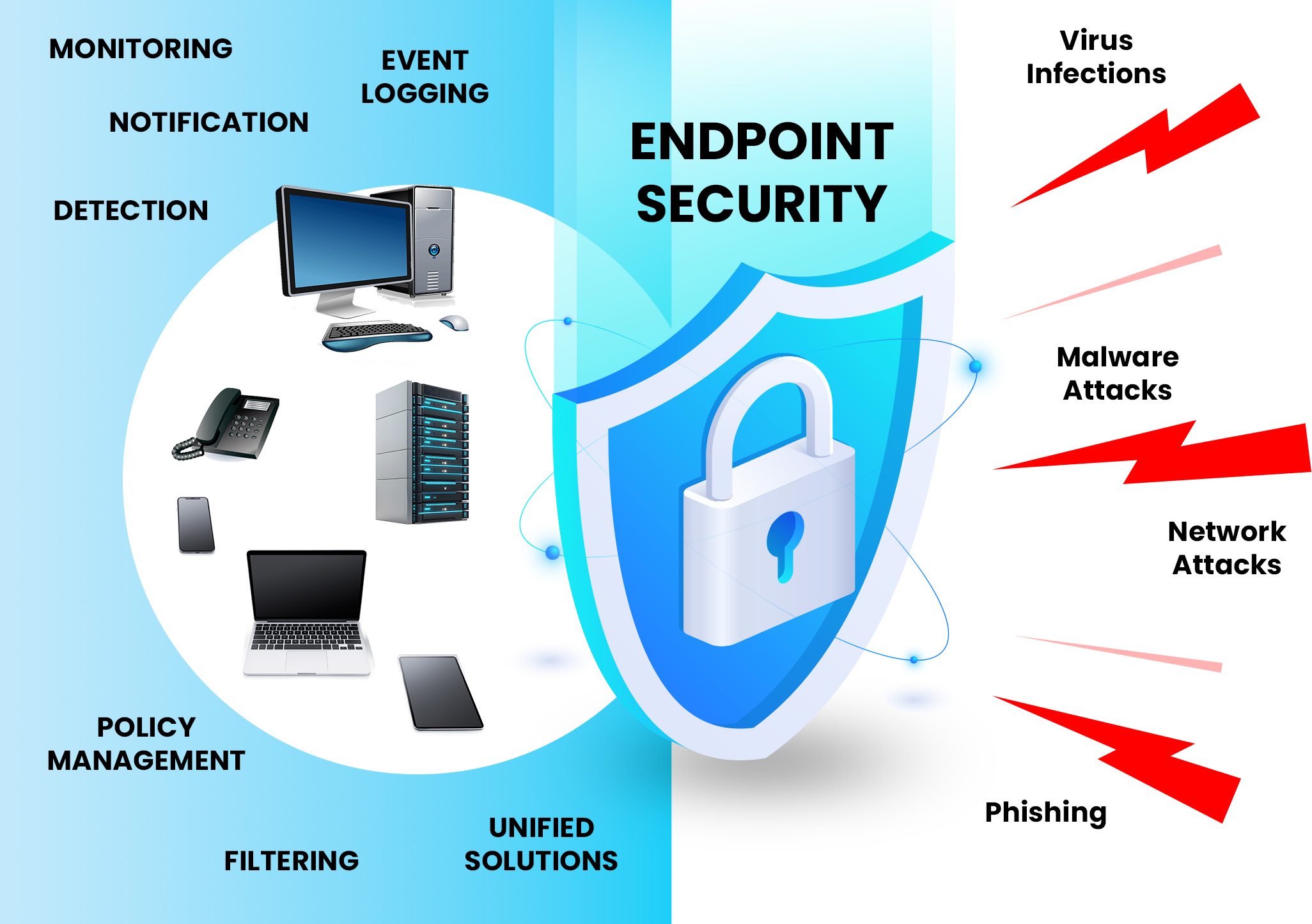
What is Endpoint Security?
Defending Connected Devices
Endpoint protection is a cybersecurity approach that defends all network-connected devices from cyber threats.
Securing Critical Assets
It secures laptops, desktops, smartphones and servers. It also protects endpoints that remotely access corporate resources.
Why Endpoint Protection Matters?
Rise of Remote Work
Remote work has significantly increased attack surfaces, making endpoints vulnerable.
Sophisticated Threats
Ransomware, phishing and data theft target endpoints. These threats are constantly evolving.
High Attack Rate
Advanced endpoint attacks are increasing. Ensuring protection is crucial.
Why choose Endpoint Security with us?
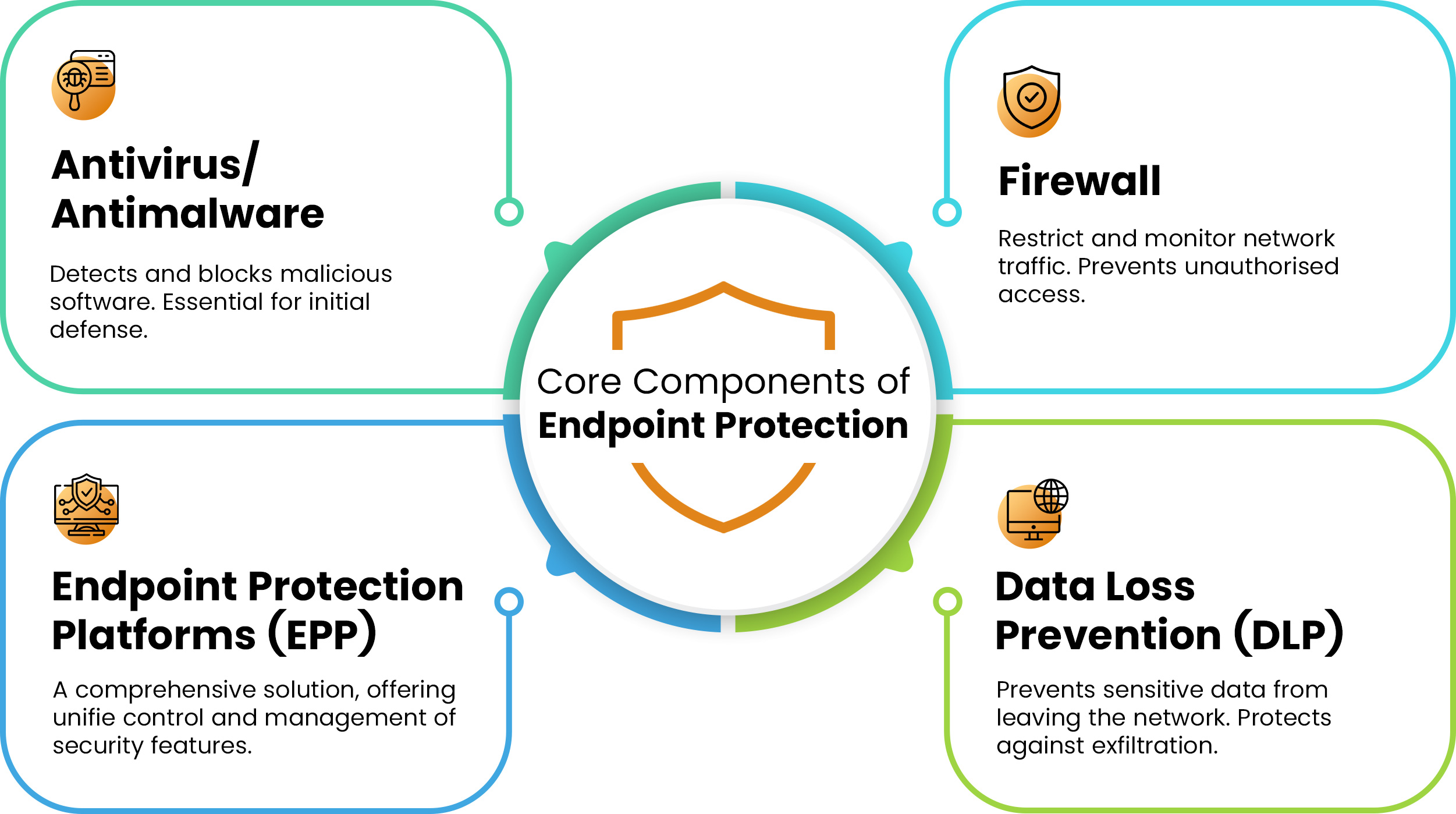
Core Components of Endpoint Protection
Advanced Endpoint Security Technologies
These advanced technologies enhance endpoint security by providing real-time intelligence, automated analysis, and comprehensive response capabilities, creating a multi-layered defense against evolving threats.
AI-Driven Detection
Leverages artificial intelligence for proactive threat detection.
Cloud Threat Databases
Utilises global, cloud-based threat intelligence for real-time updates.
Sandbox Analysis
Safely executes suspicious files in an isolated environment for analysis
Endpoint Detection & Response (EDR)
Provides tools for incident investigation and response.
Best Practices & Implementation Strategies
Effective endpoint protection requires a multi-faceted approach. Consistent maintenance and user awareness are as crucial as the technology itself.

Updates & Patching
Regularly update software and apply patches to fix vulnerabilities.

Layered Defense
Combine EPP, EDR, DLP, and firewalls for robust security.

Centralised Monitoring
Implement unified systems for monitoring and coordinated response.

User Training
Educate users on security practices and enforce strict access controls.
The Future of Endpoint Protection
The landscape of endpoint protection will continue to evolve, driven by advancements in AI and the shift towards integrated, zero-trust models. Constant adaptation will be key.
AI/ML Proactive Defense
Increased use of artificial intelligence and machine learning for predictive security.
Integrated Security
Seamless integration with network-level and cloud-native security solutions.
Zero Trust Architectures
Consolidation into holistic zero trust security frameworks.
Adaptive Protection
Ongoing need for security solutions that adapt and evolve with new threats.
Get in touch
Arrange a call with our team to find out more, get a quote and tailor a solution to your needs.